SSL transmission between IQ4docs components and to the browser
The communication of the IQ4docs components (microservices executed by IIS) as well as the call of the web interface in the browser can be encrypted. All URLs must then be specified with https://. If you are using a valid and trustworthy certificate, this will be indicated accordingly in the browser (usually by a green marking).
A certificate without Perfect Forward Secrecy (PFS) must be used (the certificate must be supported by JAVA ME 1.4). Older device models might not be able to handle all encryption levels. It is best to acquire a certificate from an official certificate authority.
To enable encrypted transmission in IIS, the certificate must be imported into the web server and entered in the binding of the default web site, see Installing SSL certificate in IIS.
If the transmission between the services is encrypted, the device also accesses the services with an HTTPS connection.
It depends on the device manufacturer whether the certificate is accepted as trusted. If not, an error message may appear on the device stating that the device cannot access the server (e.g. "Connection to destination cannot be established"). In this case, the CA certificate (Certificate Authority - this certificate confirms membership of a trusted certification authority) must be stored on the device (usually this is done via the device's web interface). If you do not know how to store the certificate on your device, contact your device support representative.
More and more device manufacturers no longer allow the mixing of unencrypted and encrypted transmissions. The connection to RabbitMQ via WebStomp protocol (ws) from the devices must then also be encrypted (wss). Otherwise, for example, the card login on the device may no longer work.
To encrypt the transfer from the device to RabbitMQ requires the following steps:
Modify the lines below in the LocalService.config of the DeviceService or add the lines before <\appSettings>.
-
<add key="RabbitMqStompUseSSL" value="true" />
Enable encryption (true).
-
<add key="RabbitMqStompPortSSL" value="15675" />
Specify the port for encrypted transmission (default: 15675).
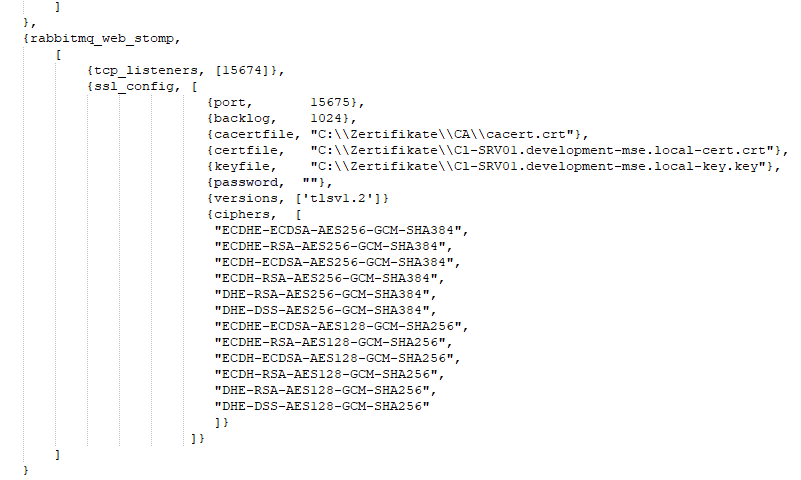
Place the certificate files (.pem and .crt and the key file .key) in a directory that the RabbitMQ service can reach. You can obtain these files from your server certificate contact person. Then make adjustments in the ssl_config section (subsection of rabbitmq_web_stomp).
-
{port, 15675}
Specify here the port that was specified in the LocalService.config of the DeviceService for RabbitMqStompPortSSL. -
{cacertfile, "c:\Certificates\cacert.crt"}
Specify the path and name of the CA certificate (Certificate Authority). This certificate confirms the affiliation with a trusted certificate authority. It is only required in certain cases (e.g. for self-signed certificates or multiple domains) and must then have been added to a trusted root certificate authority on the Windows server under Manage Computer Certificates. -
{certfile, "c:\Certificates\cert.crt"}
Specify the path and name of the server certificate. This certificate is usually issued under the hostname (FQDN) of the IQ4docs server. -
{keyfile, "c:\Certificates\key.key"}
Specify the path and name of the certificate key file. -
{password, "password"}
If the certificate's key file is password protected, specify the password here. -
{versions, ['tlsv1.2', 'tlsv1.1']}
Specify here which encryption protocols or protocol versions are allowed. In the example, these are TLS 1.1 and TLS 1.2. For example, if you no longer want to allow TLS 1.1, remove the entry from the comma-separated list (if there is only one entry left, remove the comma as well). -
{ciphers, [
"ECDHE-ECDSA-AES256-GCM-SHA384",
"ECDHE-RSA-AES256-GCM-SHA384",
"ECDH-ECDSA-AES256-GCM-SHA384",
"ECDH-RSA-AES256-GCM-SHA384",
"DHE-RSA-AES256-GCM-SHA384",
"DHE-DSS-AES256-GCM-SHA384",
"ECDHE-ECDSA-AES128-GCM-SHA256",
"ECDHE-RSA-AES128-GCM-SHA256",
"ECDH-ECDSA-AES128-GCM-SHA256",
"ECDH-RSA-AES128-GCM-SHA256",
"DHE-RSA-AES128-GCM-SHA256",
"DHE-DSS-AES128-GCM-SHA256"
]}The specification of the ciphers (encryption method) is not mandatory, but can limit the allowed encryption methods and thus provide further security here. Depending on the device manufacturer, the encryption depth is limited to 128 bits, for example.
The figure below shows a sample section of a rabbitmq.config.
Specify the protocol https in the system area used (the default is the Standard Area). Make sure that the name of the server with domain specification is specified exactly as the domain was specified in the certificate (e.g. printserver.company.com), see System Areas.
To call the WebClient and the WebAdmin, enter the URL encrypted in the LocalService.config of the WebClient (<InstallationPath>\WebClient\LocalService.config) and the WebAdmin (<InstallationPath>\WebAdmin\LocalService.config).
- Before (unencrypted): <add name="WebConfigUrl" value="http://printserver/ConfigService" />
- Now (encrypted): <add name="WebConfigUrl" value="https://printserver.company.com/ConfigService" />
To ensure that the web pages of IQ4docs can only be accessed using encryption, set the Default Web Site settings accordingly:
- Click Default Web Site in the IIS Manager.
- On the right side, in the IIS area, open the SSL settings.
- Under Client Certificates, select Accept.
Stop all application pools after the changes have been made. Then start the ConfigService application pool first. Once this has started (wait a moment), restart all other application pools.
In the web browser, now call the IQ4docs web pages with https and the exact name as it was specified in the certificate, e.g:
- Before (unencrypted): http://printserver/webadmin
- Now (encrypted): https://printserver.company.com/webadmin